
With the rise of personalized attacks and AI-generated ransomware, many traditional cybersecurity defenses are becoming less effective. We simply cannot stop an attack if the victim gets emotionally invested in making it succeed. Thus, cyber resilience becomes a significant part of the current defense against cyber attacks, and backups are a crucial part of IT.
Yet backup software receives little attention between firewalls and AI tools. Thus, let’s explore why backups are more important than ever and what business leaders should ask IT about an organization’s data strategy.
Backups as a Cyber Crime Defense
In tech, backups refer to creating a copy of your files and storing it at a different location. Traditionally, they are a defense against force acts of God, such as fire or earthquakes. By storing the data in a secondary location, a fire cannot reach every copy of the data, thus reducing the loss inflicted on an organization. They also provide a secondary defense against other incidents, such as system theft, administrative errors, or accidental deletion.
Traditionally, administrators didn’t see them as a defense against cybercrime, as they don’t provide a defense against data thefts or espionage. Yet, today, the majority of cybercrime involves ransomware attacks. Ransomware attacks involve encrypting the victim’s data, making it unusable for the owner. On a technical level, there is very little difference between deleting and encrypting the data. In both cases, the data owner doesn’t have access to it. Yet, psychologically, the encrypted data provides the little bone for the victim to pay for its release.
Once we consider encrypted data equivalent to deleted data, we can ignore the psychological call to pay for the release. Instead, we can focus on the same processes and recovery strategies we would use if a fire had destroyed the files.
Data Life Cycles
Every employee creates significant amounts of data during the workday. From a cashier ringing up a transaction on the point-of-sale system to the accountant entering transactions into a spreadsheet to programmers writing new software, they all create new data. Often, a single system, like the accountant’s notebook or the source code management system, initially stores all the data.
For files on a single endpoint, like the spreadsheet, a file storage service, like NextCloud or ownCloud, takes the files and stores them on a server. All servers, from the file storage service to the source code management system, get backed up every night in a remote location. Crucially, while the backup system stores the file ownership, the technical owners don’t have access to the backups. Thus, if ransomware compromises the original system, the users do not have the privileges to access the backups.
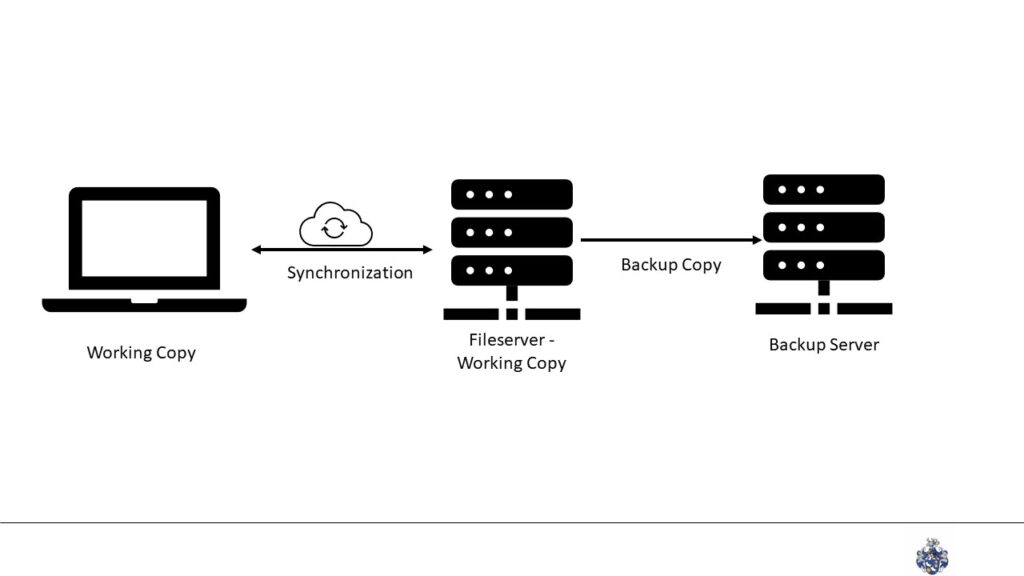
Crucially, the software should automate the backup creation without a user’s or administrator’s action. Manual action is more likely to be forgotten, changed, or mismanaged due to external events like holidays.
Please note that backups aren’t long-term archives. They have a copy of the working system to enable IT to return to a working state. Archiving is a separate topic with its legal requirements.
Questions to Ask
When thinking about backups and data retention strategies, fire is more straightforward to imagine than cybercrime. From a human perspective, a fire is much less complicated than a ransomware attack. Likewise, experts are less likely to use jargon when discussing a burned-down server room than AI-generated ransomware.
Some of the most critical questions to ask:
- How often do we make backups?
- Where do we store backups?
- Who has access to our backups?
- How long does it take to get them back into operation?
- Are our cloud services covered, either technically or contractually?
- How much work time would we lose if we had a fire in our server room or cloud service provider?
- When was the process last tested?
The first five questions cover the processes. IT should have written them down in their operations manual. While the explanation might require some probing, getting the answers reasonably quickly should be possible.
The last two questions aim at the business impact and the risk associated with rolling back data. Lost work time equals lost revenue and dissatisfied employees and customers. Thus, It should work on minimizing the time. Lastly, without testing the systems, theoretical calculations will remain pure theory. Incidents should be part of exercises and practices. Including upper management and the board in board in the next round of exercises will help foster a deeper understanding of the processes.
Start Creating Backups of Your Files
Our data is a valuable target for criminals to attack. In our rapidly digitalizing world, there is no way we can reduce our companies’ dependency on computers. We don’t have the talent or labor force to do manual double-entry bookkeeping, create designs on a simple drafting table, or manage catalog mail-in orders. Thus, reliance on technology will remain with us and probably continue to increase.
Backups can be a significant tool for enhancing cybersecurity. They can turn a drawn-out and expensive incident into an inconvenience. While a day of lost work playing back a backup will be noticeable on the bottom line, it will still be much less than the ransom criminals might demand or the issues of recreating years of data. Ultimately, they might be the tool to protect a company from collapse after an incident.
